Introduction
Earlier this evening I saw a tweet appear which claimed Monero has been hacked and a malicious binary (instead of the real one) has been served:
Warning Monero users: If you downloaded Monero in the past 24 hours you may have installed malware. Monero's official website served compromised binaries for at least 30 minutes during the past 24 hours. Investigations are ongoing. https://t.co/geqA4dIPar— dark.fail (@DarkDotFail) November 19, 2019
Post on Reddit:
https://www.reddit.com/r/Monero/comments/dyfozs/security_warning_cli_binaries_available_on/
Github issue:
https://github.com/monero-project/monero/issues/6151
Linux binary
Thanks to user nikitasius I was able to retrieve the malicious binary:
https://github.com/monero-project/monero/issues/6151#issuecomment-555511805
This binary is an ELF file with the following properties:
The seed will be sent to: node.hashmonero[.]com.
cryptonote::simple_wallet::send_to_cc
As you may have guessed, this function will send data off to the CC or C2 (command and control) server - this will be stolen funds.
Sending funds to the C2 is handled using an HTTP POST request to the following C2 servers:
As far I can see, it doesn't seem to create any additional files or folders - it simply steals your seed and attempts to exfiltrate funds from your wallet.
Windows binary
The C2 server 45.9.148[.]65 also hosts a Windows binary with the following properties:
The Windows version is essentially doing the same things as the Linux version - stealing your seed and wallet funds - the function names are just different, e.g. _ZN10cryptonote13simple_wallet9send_seedERKN4epee15wipeable_stringE.
Note: this doesn’t mean the official Windows binary was also compromised - it simply means there’s also a compromised Windows binary out there. Only the Monero team can confirm if other binaries (besides the Linux one mentioned in this blog) have been compromised.
Detection
There's an additional analysis by SerHack here:
https://serhack.me/articles/cli-binaries-compromised-monero-analysis/
The Monero team has issued a statement as follows:
Warning: The binaries of the CLI wallet were compromised for a short time:
On AlienVault:
https://otx.alienvault.com/pulse/5dd4574fc7c82cddbdcb8d12
MITRE ATT&CK techniques
ID: T1195 - Supply Chain Compromise
ID: T1199 - Trusted Relationship
https://www.reddit.com/r/Monero/comments/dyfozs/security_warning_cli_binaries_available_on/
Github issue:
https://github.com/monero-project/monero/issues/6151
Linux binary
Thanks to user nikitasius I was able to retrieve the malicious binary:
https://github.com/monero-project/monero/issues/6151#issuecomment-555511805
This binary is an ELF file with the following properties:
- MD5: d267be7efc3f2c4dde8e90b9b489ed2a
- SHA-1: 394bde8bb86d75eaeee69e00d96d8daf70df4b0a
- SHA-256: 7ab9afbc5f9a1df687558d570192fbfe9e085712657d2cfa5524f2c8caccca31
- File type: ELF
- Magic: ELF 64-bit LSB shared object, x86-64, version 1 (GNU/Linux), dynamically linked (uses shared libs), for GNU/Linux 3.2.0, from 'x)', not stripped
- File size: 27.63 MB (28967688 bytes)
- VirusTotal report: https://www.virustotal.com/gui/file/7ab9afbc5f9a1df687558d570192fbfe9e085712657d2cfa5524f2c8caccca31/summary
When comparing the legitimate file and this ELF file, we notice the file size is different, and a few new functions have been added:
cryptonote::simple_wallet::send_seed
This function is immediately called after either opening or creating a new wallet, as can be seen in Figure 1 and 2 below.
 |
| Figure 1 - Create wallet (legitimate) |
 |
| Figure 2 - Call new seed function |
The seed will be sent to: node.hashmonero[.]com.
cryptonote::simple_wallet::send_to_cc
As you may have guessed, this function will send data off to the CC or C2 (command and control) server - this will be stolen funds.
 |
| Figure 3 - Send to cc |
Sending funds to the C2 is handled using an HTTP POST request to the following C2 servers:
- node.xmrsupport[.]co
- 45.9.148[.]65
As far I can see, it doesn't seem to create any additional files or folders - it simply steals your seed and attempts to exfiltrate funds from your wallet.
Windows binary
The C2 server 45.9.148[.]65 also hosts a Windows binary with the following properties:
- MD5: 72417ab40b8ed359a37b72ac8d399bd7
- SHA-1: 6bd94803b3487ae1997238614c6c81a0f18bcbb0
- SHA-256: 963c1dfc86ff0e40cee176986ef9f2ce24fda53936c16f226c7387e1a3d67f74
- File type: Win32 EXE
- Magic: PE32+ executable for MS Windows (console) Mono/.Net assembly
- File size: 65.14 MB (68302960 bytes)
- VirusTotal report: https://www.virustotal.com/gui/file/963c1dfc86ff0e40cee176986ef9f2ce24fda53936c16f226c7387e1a3d67f74/summary
The Windows version is essentially doing the same things as the Linux version - stealing your seed and wallet funds - the function names are just different, e.g. _ZN10cryptonote13simple_wallet9send_seedERKN4epee15wipeable_stringE.
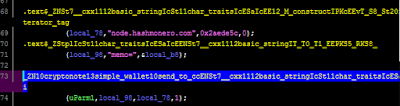 |
| Figure 4 - Send to cc |
Note: this doesn’t mean the official Windows binary was also compromised - it simply means there’s also a compromised Windows binary out there. Only the Monero team can confirm if other binaries (besides the Linux one mentioned in this blog) have been compromised.
Detection
- If you have a firewall or proxy, whether hardware or software, verify if you had any network traffic or connections to;
- node.hashmonero[.]com
- node.xmrsupport[.]co
- 45.9.148[.]65
- 91.210.104[.]245
- Remove all the binaries listed in this blog post;
- Verify the hashes of your Monero setup or installer file. Guides to do that here;
- Beginner: https://src.getmonero.org/resources/user-guides/verification-windows-beginner.html
- Advanced: https://src.getmonero.org/resources/user-guides/verification-allos-advanced.html
- Note: hashes list is available here: https://web.getmonero.org/downloads/hashes.txt.
Note: What is a hash? A hash is a unique identifier. This can be for a file, a word, ... It is preferred to use SHA256 hashes for file integration checks, as it is more secure.
You may also use the following Yara rule to detect the malicious or compromised binaries:
There's an additional analysis by SerHack here:
https://serhack.me/articles/cli-binaries-compromised-monero-analysis/
Recommendations
- Install an antivirus, and if possible, use a firewall (free or paid is of less importance);
- If you already use an antivirus: it may be a good idea to not exclude a specific folder in your antivirus when using Monero (or other miners), and if needed, only do so after the hashes have been verified;
- Restore your seed or account;
- How to restore your account: https://web.getmonero.org/resources/user-guides/restore_account.html
- Recovering wallet using the mnemonic seed: https://monero.stackexchange.com/questions/10/how-can-i-recover-a-wallet-using-the-mnemonic-seed
- Monitor your account/wallet for the next days and verify there have been no fraudulent transactions. Contact the Monero team for support.
Note: Especially go through the steps if at any point you downloaded, used or installed new binaries between these dates: Monday 18th 1:30 AM UTC and 5:30 PM UTC. Download the latest version from: https://web.getmonero.org/downloads/.
Monero team statement
Monero team statement
The Monero team has issued a statement as follows:
Warning: The binaries of the CLI wallet were compromised for a short time:
https://web.getmonero.org/2019/11/19/warning-compromised-binaries.html
I expect this statement to be updated the following days, so monitor it as well.
I expect this statement to be updated the following days, so monitor it as well.
Conclusion
Monero is not the first, nor will it likely be the last cryptocurrency (in this case, its website and binaries) that gets compromised.
Follow the steps in this blog post to protect yourself and always watch your online accounts closely, especially those where you have financially invested in. Use strong passwords, use MFA (or 2FA) where possible and always be vigilant. Verify hashes when a new version is available.
Note: this blog post is not intended to be a full analysis, but rather a quick report on the facts, including recommendations. Questions or feedback? Happy to hear it!
Let me know in the comments below or on Twitter.
Monero is not the first, nor will it likely be the last cryptocurrency (in this case, its website and binaries) that gets compromised.
Follow the steps in this blog post to protect yourself and always watch your online accounts closely, especially those where you have financially invested in. Use strong passwords, use MFA (or 2FA) where possible and always be vigilant. Verify hashes when a new version is available.
Note: this blog post is not intended to be a full analysis, but rather a quick report on the facts, including recommendations. Questions or feedback? Happy to hear it!
Let me know in the comments below or on Twitter.
Indicators
| Indicator type | Indicator |
|---|---|
| FileHash-SHA256 | 7ab9afbc5f9a1df687558d570192fbfe9e085712657d2cfa5524f2c8caccca31 |
| FileHash-SHA256 | 963c1dfc86ff0e40cee176986ef9f2ce24fda53936c16f226c7387e1a3d67f74 |
| hostname | www.hashmonero.com |
| hostname | node.xmrsupport.co |
| hostname | node.hashmonero.com |
| FileHash-MD5 | d267be7efc3f2c4dde8e90b9b489ed2a |
| FileHash-MD5 | 72417ab40b8ed359a37b72ac8d399bd7 |
| FileHash-SHA1 | 6bd94803b3487ae1997238614c6c81a0f18bcbb0 |
| FileHash-SHA1 | 394bde8bb86d75eaeee69e00d96d8daf70df4b0a |
| IPv4 | 91.210.104.245 |
| IPv4 | 45.9.148.65 |
| domain | hashmonero.com |
| domain | xmrsupport.co |
On AlienVault:
https://otx.alienvault.com/pulse/5dd4574fc7c82cddbdcb8d12
MITRE ATT&CK techniques
ID: T1195 - Supply Chain Compromise
ID: T1199 - Trusted Relationship
Thanks for your analysis! Can you please tell which software you used to decompile the functions?
ReplyDeleteghidra
DeleteThanks Paul! It's indeed Ghidra - get it from here: https://ghidra-sre.org/
DeleteThank you Bart.
ReplyDeleteMy pleasure!
DeleteWallet working fine !!! This is a Fake news !!! Not worry ...
ReplyDeleteThanks for your comment. Please re-read the blog post.
DeleteThank you for the analysis!
ReplyDeleteThanks Arri! :)
Delete