Do you love the smell of phishing in the morning? I surely don't. In today's post we will be reviewing a phishing attempt for Diablo or Diablo III.
The following mail ended up in my mailbox:
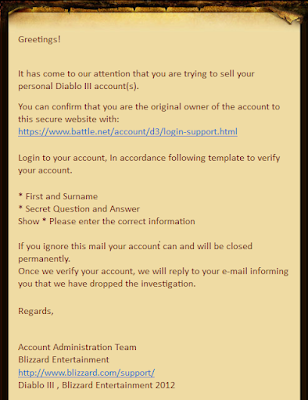 |
| You need to login as soon as possible to avoid account closing |
There are other, less fancy examples:
 |
| Same trick as in the previous example. You need to "verify" your account |
Subjects of the mail can vary, but these are the most common:
- Blizzard Notification About Diablo III Account
- Diablo III Account-Notice
- Diablo III Account - login validation
- You must verify your identity as the registered account .World of Warcraft - Diablo III account (s).
The introduction in the email reads:
Greetings! It has come to our attention that you are trying to sell your personal Diablo III account(s). As you may not be aware of, this conflicts with the EULA and Terms of Agreement. If this proves to be true, your account can and will be disabled. It will be ongoing for further investigation by Blizzard Entertainment's employees. If you wish to not get your account suspended you should immediately verify your account ownership.
Let's move on to the actual link in the phishing mail. When clicked you'll land on the following page:
 | |||
| An exact copy of the real login page at Battle.net |
Below you can find the list of URLs I've gathered in the past days, do not visit any of them as they may harm your computer (or even worse, your Diablo account ;-) ).
hxxp://battle.net.noreply-login.com
hxxp://cn15mcc.com
hxxp://eu.diablo.net.account.oy-login.in
hxxp://eu.diablo.net.account.ts-login.in
hxxp://eu.diablo.net.ca.zx-login.in
hxxp://eu.diablo.net.jiagedi.info
hxxp://eu.diablo.net.tianzhou58.info
hxxp://us.battle.com.wwowus.com
hxxp://us.battle.net.aacc.cn.com
hxxp://us.battle.net.cacc.cn.com
hxxp://us.battle.net.ccus.asia
hxxp://us.battle.net.ddeu.asia
hxxp://us.battle.net.eacc.cn.com
hxxp://us.battle.net.en.oo-rs.com
hxxp://us.battle.net.en.qq-rs.com
hxxp://us.battle.net.en.uu-rs.com
hxxp://us.battle.net.facc.cn.com
hxxp://us.battle.net.ffus.asia
hxxp://us.battle.net.gacc.cn.com
hxxp://us.battle.net.ggwow.asia
hxxp://us.battle.net.hhwow.asia
hxxp://us.battle.net.iacc.cn.com
hxxp://us.battle.net.iieu.asia
hxxp://us.battle.net.jacc.cn.com
hxxp://us.battle.net.kacc.cn.com
hxxp://us.battle.net.lacc.cn.com
hxxp://us.battle.net.lacc.cn.com
hxxp://us.battle.net.llus.asia
hxxp://us.battle.net.login.en.ddus.asia
hxxp://us.battle.net.login.en.yykiki.com
hxxp://us.battle.net.login.en.zkiki.com
hxxp://us.battle.net.ok.jjweb.asia
hxxp://us.battle.net.ok.kk-rs.com
hxxp://us.battle.net.ok.qw-rs.com
hxxp://us.battle.net.ok.uuweb.asia
hxxp://us.battle.net.ok.yywow.asia
hxxp://us.battle.net.pacc.cn.com
hxxp://us.battle.net.ppwow.asia
hxxp://us.battle.net.qacc.cn.com
hxxp://us.battle.net.racc.cn.com
hxxp://us.battle.net.rreu.asia
hxxp://us.battle.net.tacc.cn.com
hxxp://us.battle.net.uacc.cn.com
hxxp://us.battle.net.uuwow.asia
hxxp://us.battle.net.w.llweb.asia
hxxp://us.battle.net.wacc.cn.com
hxxp://us.battle.net.w-u.asia
hxxp://us.battle.net.xacc.cn.com
hxxp://us.battle.net.yacc.cn.com
hxxp://us.battle.net.zacc.cn.com
hxxp://us.battle.net-bizzard-d3-com.account-com.net
hxxp://us.diablo.net.en.rk-login.in
Most of the domains seem to be set up by the same person, someone named "Jin Yu":
Registrant Contact:
Jin Yu
Yu Jin jinyu2000@yahoo.cn
+86.324242434233 fax: +86.324242434233
ShengLiLu
Shangraoshi Jiangxi 610041
CN
Other email addresses associated with Jin Yu:
329409115@qq.com
service@511web.com
Almost all of the IP addresses are originating from China. The hosting companies are as follows, and seem to not care (or know) that malware and phishing pages are set up:
Beijing Weishichuangjie Technical Development Co. - IPvoid Result
DEEPAK MEHTA FIE - IPvoid Result
New World Telecom Ltd., Hong Kong - IPvoid Result
XIN XIN LING - IPvoid Result
Thanks to IPvoid you can easily see other sites hosted there, seems there is more of the same. (read: more malware & phishing pages are hosted)
Conclusion
Stay away from phishing mails like the ones pointed out in this post. There are several variants, some more graphical than others, but in the end they serve the same purpose:
Trying to steal your login credentials!
I'm sure that even when you open the mail, alarm bells should be going off if you simply check the URL, it's pointing to another address than the usual login page.
To be clear, the real webpage to login for your Battle.net account is:
https://battle.net/login/en/
If you're ever in doubt, visit the website directly and do not click on any links in emails from unknown senders. Use add-ons like WoT and/or NoScript to stay protected against these types of threats.
You can also use the URL scanning services at VirusTotal or URLvoid to double-check a URL.
That email message is really suspicious!
ReplyDeleteMining in groups is a better choice for the players. You will find that players who my own in groups may have obvious roles split in.
ReplyDelete