CryptoWire is an "open-source" ransomware based on the AutoIT scripting language, and has been around since 2016. For some background, read the following post on Bleeping Computer:
"Proof of Concept" CryptoWire Ransomware Spawns Lomix and UltraLocker Families
I already encountered a CryptoWire variant last year, when it was used to target users in Brazil:
Ransomware, fala sério!
In this blog post, we'll briefly analyse another, recent, CryptoWire sample.
Analysis
This CryptoWire variant has the following properties:
- MD5: f6d01e72a58a8bdf14f9a103250f779e
- SHA1: 3b97bac22a04282ebbaef60beb168a41e4449239
- SHA256: 4deff7d8434583ea8e5c3ef9b4c64674dfb165b1720ddf63b5abdd8ed6a7399c
- Compilation timestamp: 2018-04-10 16:00:12
- VirusTotal report:
4deff7d8434583ea8e5c3ef9b4c64674dfb165b1720ddf63b5abdd8ed6a7399c
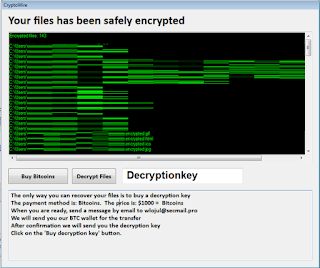 |
| Figure 1 - Typical CryptoWire layout |
The message reads:
The only way you can recover your files is to buy a decryption key
The payment method is: Bitcoins. The price is: $1000 = Bitcoins
When you are ready, send a message by email to wlojul@secmail.pro
We will send you our BTC wallet for the transfer
After confirmation we will send you the decryption key
Click on the 'Buy decryption key' button.
CryptoWire will encrypt files with the following extensions (282 total):
3fr, 7z, EPS, M3U, M4A, PEM, PSD, WPS, XLSX, abw, accdb, afsnit, ai, aif, arc, arw, as, asc, asd, asf, ashdisc, asm, asp, aspx, asx, aup, avi, bay, bbb, bdb, bibtex, bkf, bmp, bmp, bpn, btd, bz2, c, cdi, cdr, cer, cert, cfm, cgi, cpio, cpp, cr2, crt, crw, csr, cue, dbf, dcr, dds, dem, der, dmg, dng, doc, docm, docx, dsb, dwg, dxf, dxg, eddx, edoc, eml, emlx, eps, epub, erf, fdf, ffu, flv, gam, gcode, gho, gpx, gz, h, hbk, hdd, hds, himmel, hpp, ics, idml, iff, img, indd, ipd, iso, isz, iwa, j2k, jp2, jpeg, jpf, jpg, jpm, jpx, jsp, jspa, jspx, jst, kdc, key, keynote, kml, kmz, lic, lwp, lzma, m4v, max, mbox, md2, mdb, mdbackup, mddata, mdf, mdinfo, mds, mef, mid, mov, mp3, mp4, mpa, mpb, mpeg, mpg, mpj, mpp, mrw, msg, mso, nba, nbf, nbi, nbu, nbz, nco, nef, nes, note, nrg, nri, nrw, odb, odc, odm, odp, ods, odt, ogg, one, orf, ova, ovf, oxps, p12, p2i, p65, p7, p7b, p7c, pages, pct, pdd, pdf, pef, pem, pfx, php, php3, php4, php5, phps, phpx, phpxx, phtm, phtml, pl, plist, pmd, pmx, png, ppdf, pps, ppsm, ppsx, ppt, pptm, pptx, ps, psd, pspimage, pst, ptx, pub, pvm, qcn, qcow, qcow2, qt, r3d, ra, raf, rar, raw, rm, rtf, rtf, rw2, rwl, s, sbf, set, skb, slf, sme, smm, snp, spb, sql, sr2, srf, srt, srw, ssc, ssi, stg, stl, svg, swf, sxw, syncdb, tager, tc, tex, tga, thm, tif, tiff, til, toast, torrent, txt, vbk, vcard, vcd, vcf, vdi, vfs4, vhd, vhdx, vmdk, vob, vsdx, wav, wb2, wbk, wbverify, webm, wmb, wpb, wpd, wps, x3f, xdw, xlk, xlr, xls, xlsb, xlsm, xlsx, xz, yuv, zip, zipx
It will also encrypt files, regardless of extension, in certain folders such as Desktop.
Files are encrypted with AES, and prepends extension of encrypted files with ".encrypted.". For example: Tulips.encrypted.png.
CryptoWire will delete Shadow Volume Copies and disable BCDEdit by executing these commands:
It will additionally create a scheduled task for persistence.
vssadmin.exe Delete Shadows /All /Quietbcdedit /set {default} recoveryenabled Nobcdedit /set {default} bootstatuspolicy ignoreallfailures
It will additionally create a scheduled task for persistence.
You can decrypt files for this specific variant with the following Decryption Key:
VgjRPoOM0oa92_jId!/wkMeW6,guuSe
VgjRPoOM0oa92_jId!/wkMeW6,guuSe
Conclusion
Some ransomware variants simply do not die, one example of these appears to be CryptoWire. If you have been hit by this particular strain, use the decryption key as instructed above, and your files will be decrypted.
Make sure to read the dedicated page on ransomware prevention to prevent CryptoWire or any other "open-source" ransomware to infect your machine, and encrypt your files.
IOCs
No comments:
Post a Comment